USGov RMF Series: USGov Cybersecurity Regulatory Landscape (FISMA Compliance)
The US Government (USGov) Cybersecurity Risk Management landscape can be very challenging to navigate. Government agencies and their service providers are often overwhelmed by the vast amount of information and resources required to satisfy USGov cybersecurity requirements. Given that these requirements are law and policy-driven, implementers like software engineers find it even more challenging to follow due to the lack of processes that translate laws and policies into actionable tasks. These tasks are essential for engineers and developers to design, implement, and configure US government systems and software. To fully understand the US cybersecurity landscape, it is crucial to comprehend the most critical cybersecurity laws and frameworks that affect all US federal agencies.
This blog series aims to demystify US government cybersecurity laws, policies, and frameworks by mapping and translating USGov cybersecurity requirements. This mapping and translation will guide agency stakeholders, risk professionals, software developers, and implementation engineers to better understand the security requirements for developing and implementing cybersecurity solutions intended for US government use.
US Cybersecurity Governance and Risk Management
FISMA: The Federal Information Security Management Act of 2002 (FISMA) is a federal law that requires each federal agency to develop, document, and implement an agency-wide program to secure the information and systems that support the operations and assets of the agency, including those provided or managed by another agency or contractor. In 2014, FISMA was amended to become the Federal Information Security Modernization Act of 2014 (FISMA of 2014).
Even though securing US federal government data, systems, and networks has always been part of US government agencies’ best practices, there was no mandate before FISMA. Agencies often approached security based on their culture and their leadership’s understanding of risk. This lack of uniformity resulted in some agencies, like national security agencies, having a more mature security process than other non-sensitive agencies (mostly the federal civilian agencies).
FISMA requires all US federal agencies to strengthen the security posture and reduce the cybersecurity risk of agency-wide information systems through the development, implementation, assessment, monitoring, and modernization of information system security controls following a formal usage authorization by the agency leadership, known as the Authority to Operate (ATO) process.
FISMA requirements for managing cybersecurity risks include a formal documented system security package that addresses purpose, scope, roles, responsibilities, management commitment, coordination, and clear procedures to maintain security controls. Frameworks (known as Risk Management Frameworks) exist to provide the necessary guidance to any entity on how best to secure all systems that receive, process, store, display, or transmit US government information.
Risk Management Framework (RMF) provides a disciplined and structured process that combines information system security and risk management activities into the system development life cycle. The current USGov risk management processes have changed from a static methodology known as Certification and Authorization (C&A) to a dynamic procedural activity approach known as Assessment & Authorization (A&A). The A&A process proves to be more effective in managing information system-related security risks in diverse environments of complex, ever-increasing system vulnerabilities and sophisticated cyber threats. The NIST 800-37 RMF provides the following characteristics:
- Promotes the concept of ongoing risk management and continuous information system authorization through the implementation of continuous monitoring processes.
- Encourages the use of automation to provide senior leaders with the necessary information to make cost-effective, risk-based decisions about the organizational information systems supporting their core missions and business functions.
- More fully integrates information security into the enterprise architecture and system development life cycle.
- Promotes reciprocity and reuse of test results and assessment documentation as the norm, thus saving time and resources while enhancing interoperability.
- Links risk management processes at the information system level to risk management processes at the organizational level through a risk executive (function).
- Establishes responsibility and accountability for security controls deployed within organizational information systems and inherited by those systems (i.e., common controls).
RMF for Different USGov Communities
While FISMA has the common overall objective of strengthening the security posture and reducing the overall cybersecurity risk to US Federal Government Information Systems, the journey to achieve such a goal differs across the various USGov communities.
The figure below maps the five major USGov communities and the risk management methodologies they follow:
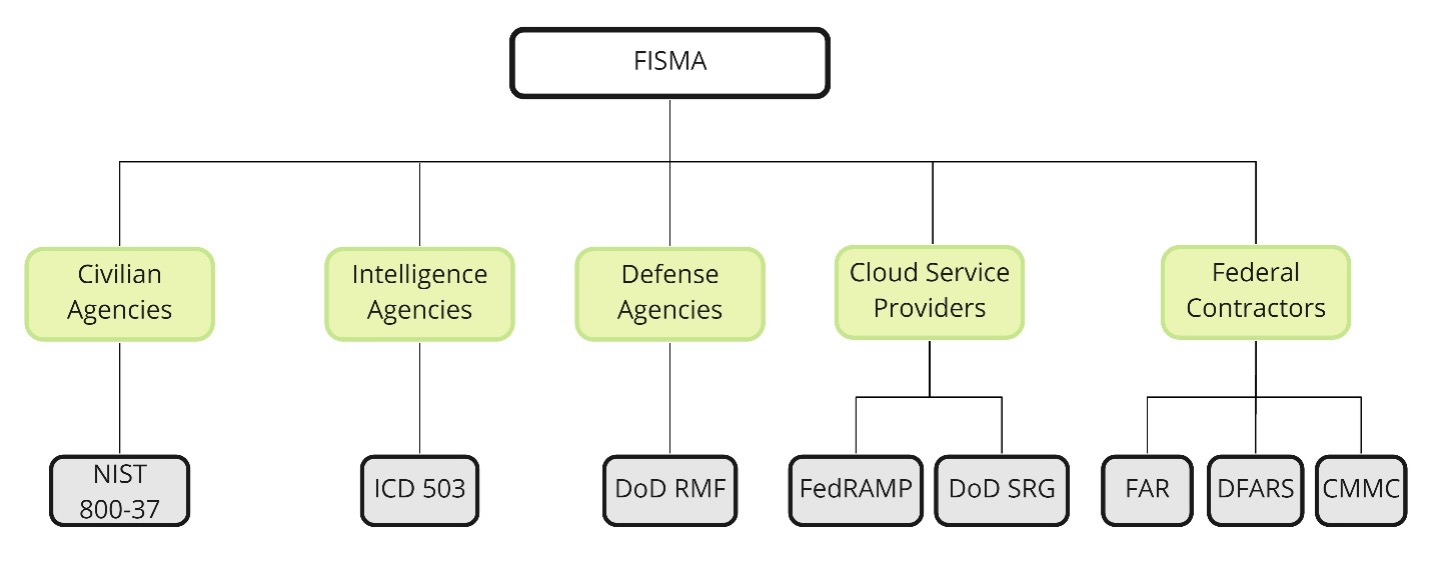
- Civilian Agencies (FedCiv): Follow the NIST SP 800-37 RMF.
- Intelligence Communities (IC): Follow the ICD-503 Security Risk Management process.
- Defense Agencies: Follow the DoD Risk Management Framework.
- Cloud Service Providers:
- Follow the FedRAMP process for civilian agency consumption.
- Follow the DISA DoD SRG for national security communities.
- Federal Contractors:
- Follow the Federal Acquisition Regulation (FAR) for civilian agencies’ Controlled Unclassified Information (CUI) by implementing NIST SP 800-171.
- Follow the Defense Federal Acquisition Regulation Supplement (DFARS) for Defense CUI by self-assessment.
- Obtain Cybersecurity Maturity Model Certification (CMMC) to establish their maturity to serve the Defense community through a third-party assessment organization.
In subsequent blogs, we will dive deeper into how each community satisfies the different cybersecurity risk governance, management, compliance, implementation, and monitoring requirements.